When Cyber Supply Chain vulnerabilities are mentioned, most people immediately recall front-page coverage of attacks like the 2020 SolarWindsi incident, where the company’s Orion platform was a victim of a supply chain attack that affected thousands of systems and customers on a global scale. What followed was nothing short of a digital storm, affecting approximately 18,000 SolarWinds customer networks, systems, and data, government agencies, and several major corporations – including government organizations like Homeland Security, State, Commerce, and Treasury, along with major private companies like FireEye, Microsoft, Intel, Cisco, and Deloitte. The aftermath of the hack indicated that U.S. businesses and government agencies spent $100 billionii to contain and fix the damage from the attack. However, that incident was not atypical. According to a study by the University of Maryland’siii Clark School, a cyber-attack occurs approximately every 39 seconds on average. A staggering amount of 44 data recordsiv are under attack each second. By the time you finish reading this paragraph, cyber criminals have stolen over 1,000 records.
Cybersecurity Venture projects a ransomware every 2 seconds by 2031 – attacks that will cost us $265B annuallyv.
The United States ranks among the top five countries and regions with the highest average data breach costs, estimated at approximately $9.44 millionvi. Almost a third of these destructive or ransomware attacks are on critical infrastructure organizations, which include financial services, industries, technology, transportation, energy, communication, healthcare, education, and public sector. Data breach on critical infrastructure poses a significant threat to citizens, businesses, and the economy as these organizations provide essential services vital to our daily lives. For example, a breach at a financial services organization could lead to the theft of financial information, such as credit card numbers and Social Security numbers. This breach could make it difficult for citizens to get loans, mortgages, and other financial services. A breach at a healthcare organization could lead to the theft of medical records, which could be used for identity theft or to blackmail citizens. An attack on the power grid could lead to widespread blackouts, disrupting hospitals, businesses, and homes.
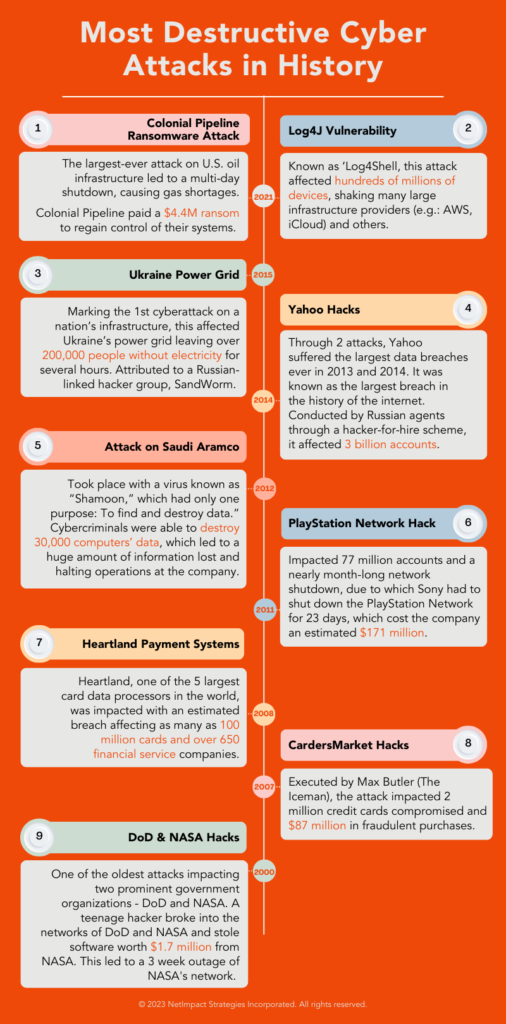
While the 2021 Colonial Pipeline cyber-attackvii did not make headlines as prominently as SolarWinds, it actually left a heavier impact on the United States and sparked global concern. The major pipeline system, spanning over 5,500 miles that supplies gasoline, diesel, and jet fuel from the Gulf Coast to the eastern U.S., was targeted by a ransomware attack causing significant economic fallout extending to both the company and the nation. Not only did it disrupt the flow of gasoline and jet fuel across the nation, leading to fuel shortages and spike in prices, the event caused a significant financial loss of over billions of dollars, affecting consumers and businesses alike. It was certainly a wake-up call to how vulnerable essential services are in the digital age. To regain control, Colonial Pipeline was forced to pay $4.4 million in cryptocurrency to the hacker group. These alarming statistics indicate the potential for cyber-attacks to inflict financial crises and is also a clear reminder of the urgency in implementing a robust cybersecurity measure to protect our critical infrastructure.
Businesses v. Bad Actors: The Struggle for Power, Control, and Money
The endgame for bad actors is to gain control of something valuable, which they achieve through a cyber-attack. A cyber-attack is a malicious attempt to damage, disrupt, or steal data from a computer system or network. Cyber-attacks are conducted by an individual or organization to compromise the confidentiality, integrity or availability of information or computer systems. Attackers use different methods to break into computer systems with different motives, including – personal, criminal, and political. Some of the most common cyber-attacks include:
Malware/ Spyware: Malware is malicious software (e.g.: viruses, worms, trojans) that can damage, disable, steal data, or cause harm to computer systems. It can be spread through email attachments, infected websites, or USB drives.
Phishing Attacks: Phishing attacks are attempts to trick users into revealing sensitive information, such as passwords or credit card numbers. Phishing emails often appear to be from legitimate companies, such as banks or government agencies.
Ransomware: These attacks encrypt an organization’s data and deny access to them to demand a ransom payment. If the victim does not pay the demanded ransom, the data is lost forever.
Identity-Based Attacks: Also known as identity theft, these attacks involve the unauthorized use of an individual’s personal information for malicious purposes. These attacks can lead to financial fraud, legal issues, and damage to one’s reputation. Common forms include financial identity theft, criminal identity theft, medical identity theft, and account takeovers.
Denial of Service Attacks (DoS): These attacks are attempts to overload a computer system or network with traffic, making it unavailable to legitimate users. There are several forms of DoS attacks, like – Flooding attacks, where attackers flood the target system with Internet Control Message Protocol (ICMP) echo requests, overwhelming its bandwidth and resources. Another example is HTTP floods, where an excessive number of HTTP requests to the target overwhelms its web servers.
Dehabiltiating Effects
These cyber-attacks sound simple in description but carry complex and destructive effects. Below are the topmost expensive cyber-attacks in recent history.
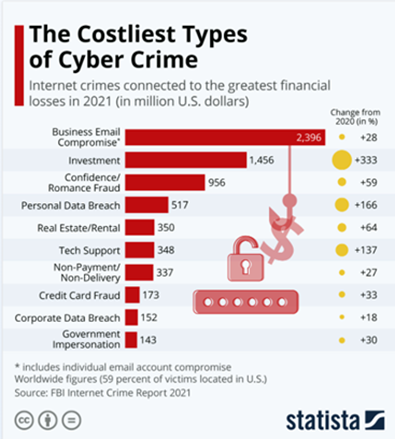
Cyber-attacks do not discriminate, so all businesses and individuals are vulnerable to its dangerous and destructive impact, which includes major financial losses, business operation disruption, and more. One of the major recoveries from these attacks is often the financial damage to businesses. A report by Statistaviii estimates global losses of $7.1 trillion in 2022 compared to 2019’s $1.2 trillion, a 491.67% increase over just one year.
From energy to healthcare, several critical infrastructure industries are vulnerable to cyber breaches, and the ramifications are far-reaching. The most targeted are healthcare, Government agencies, financial technology and insurance, education, retail, energy, and utility companies – a few are highlighted below:
Healthcare: Research shows that IT incidents are the most prevalent forms of attack behind healthcare data breaches. In a 2022ix incident, cybercriminals exposed about 50 million health records of Americans in There were nearly 28.5 million Americans affected by this breach. The Florida Healthy Kids Corporation incident in 2020x resulted in the exposure of the personal information of 3.5 million people.
Government Agencies: Government agencies possess critical infrastructures like they keep tax records of people, social security numbers, health records, etc. Cyberattacks on agencies can have severe implications and financial losses to not only themselves but on citizens. The U.S. government suffered several ransomware attacks over the last four years, affecting about 230 million people and costing about $70.4 billionxi in downtime and recovery.
Financial Technology and Insurance: FinTech and insurance companies own sensitive financial data of individuals and businesses, due to which cybercriminals target them. Moreover, the global economy depends on these sectors. In 2017, the credit reporting company Equifaxxii was breached as it failed to take reasonable steps to secure its network, affecting 147 million customer’s names, social security numbers, birth dates, and addresses. The company had to pay $575 million as part of the settlement with the Federal Trade Commission, the Consumer Financial Protection Bureau (CFPB), and 50 U.S. states and territories.
Education: Educational institutions can suffer a devastating impact from cybercrimes. They can disrupt classes, steal sensitive student and staff data, and damage the institute’s reputation. A reportxiii states that there have been 2,691 data breaches in educational institutions since 2005, affecting over 31 million individuals’ records.
How Protected is the U.S. Government from These Attacks?
The answer is not very: the current state of cyber-attacks in the U.S. Federal agencies is alarming. As industries are moving towards a more digital infrastructure, cyber threats have become more and more prevalent. Sophisticated adversaries have come a long way and have become much more advanced in planning and executing these attacks. Federal IT leaders face several challenges in mitigating these sophisticated threats that include ransomware attacks, phishing, and state-sponsored intelligence.
Recent Incidents
In June 2023, the U.S. Department of Energy and several other federal agencies were hitxiv in a global hacking campaign where data was compromised at two entities within the energy department when hackers gained access through a security flaw in MOVEit Transfer. Effected entities were DOE contractor Oak Ridge Associated Universities, and the Waste Isolation Pilot Plant – the New Mexico-based facility for disposal of defense-related nuclear waste. The incident also hit the British energy giant Shell, the University System of Georgia, the Johns Hopkins University and the Johns Hopkins Health System.
In 2021, Pottawatomie County, Kansas was hitxv by a ransomware attack where the attackers demanded $1 million to release control of the county’s data. It continued for two weeks affecting 150 desktops and laptop computers. Pottawatomie County officials agreed to pay a ransom of $71,606.25 as a bargain considering the asking price. Following the incident, the IT team swiftly implemented extra sensors on the county’s servers and pressed forward with their inquiry to uncover the methods employed by the attackers to breach their defenses.
In 2019, the city of Burlington fell victim to a $503,000xvi phishing scheme. The city staff received a complex phishing email requesting to change banking information for an established city vendor, resulting in a transfer of around $503,000 to a falsified bank account for the vendor. Upon discovering the fraudulent activity, the city promptly informed their bank and local law enforcement. Furthermore, they bolstered their internal controls, although the specifics of these enhancements remain undisclosed, in a proactive measure to prevent a recurrence of the incident.
In 2019 again, another attack began when an employee in the police department opened an infected email which took the City of Reviera’s main computer system offline, affecting every department. To secure the safe return of stolen data taken during the ransomware attack, city council members approved the payment of a $600,000 ransomxvii, payable in bitcoins by the city’s insurance company. Additionally, the city agreed to spend almost $1 million to upgrade computer equipment, including the purchase of 310 new desktops and 90 laptop computers.
These incidents serve as distressing reminders of the evolving threat landscape and the pressing need for robust cybersecurity measures at all levels of government and industry. As digital dependence deepens, it is paramount to institute proactive defence strategies and maintain unwavering vigilant responses to safeguard critical systems and sensitive data from the ever-evolving realm of cyber adversaries.
Federal Initiatives towards a Unified Defense Response
Federal agencies play a pivotal role in the realm of cybersecurity, involving both securing federal information systems and assisting in protecting non-federal systems. These roles are intricate and evolving, and often involve complex inter-agency collaboration.
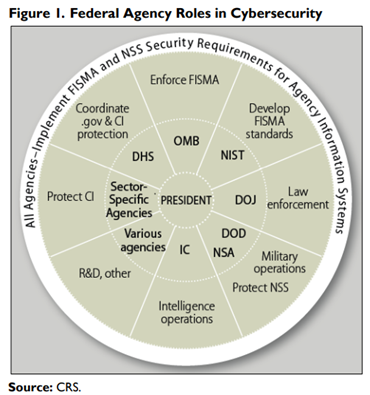
Most are familiar with Federal Information Security Modernization Act (FISMA), a law enacted in 2022 that requires all federal agencies to protect their own systems per approved framework and standards, and many agencies have sector-specific responsibilities, with some of the key federal agencies involved in cybersecurity including Office of Management and Budget (OMB), Department of Homeland Security (DHS), National Institute of Standards and Technology (NIST), Department of Justice (DOJ), Department of Defense (DOD), Intelligence Community (IC), National Security Agency (NSA), and Federal Bureau of Investigation (FBI). Additionally, agency heads across the government, e.g.: Chief Information Officers (CIOs), establish and implement agency information security programs in compliance with federal requirements while certain individual U.S. states have issued their own directives.
Newer legislations such as the Cyber Incident Reporting for Critical Infrastructure Act of 2022 (CIRCIA), signed into law in March 2022, demonstrates increased efforts to strengthen critical infrastructure cybersecurity and the crucial demand for public-private collaboration. CIRCIA prioritizes the strengthening of the cybersecurity posture of critical infrastructure from cyber-attacks for our nation, standardizes implementation expectations, and is our government’s call to action for a unified response approach.
Navigating Fiscal Challenges and Resource Constraints
As federal agencies confront the ever-evolving landscape of cyber threats, they also navigate through a complex web of fiscal challenges and resource constraints, demanding increased budget allocations. These budgeting demands encompass costs related to incident response, system remediation, legal compliance, and cybersecurity workforce development. Additionally, investments in cybersecurity technologies, information sharing, and collaboration are essential. Some of the challenges and constraints faced by federal agencies include:
Budget constraints: This poses a significant hurdle for federal agencies. Cyber security is a resource-intensive endeavour, and federal agencies are often underfunded, making it difficult for agencies to invest in the necessary technologies and personnel to protect their systems and data from cyber-attacks. The cost of cyber-attacks is also significant. Federal agencies often have to spend millions of dollars to recover from a cyber-attack, including the cost of restoring systems, investigating the attack, and implementing new security measures.
Talent shortages: There is a shortage of qualified cybersecurity professionals in the United States. This makes it difficult for federal agencies to recruit and retain the talent they need to protect their systems and data from cyber-attacks. The high demand for cybersecurity professionals is also driving up salaries, which can make it even more difficult for federal agencies to compete for top talent.
Data security: Federal agencies hold a vast amount of sensitive data, including personal information about citizens, classified information, and financial data. This data is a valuable target for cyber attackers. Data breaches can have a significant financial impact on federal agencies. In addition to the cost of recovering from a data breach, agencies may also be liable for damages to individuals whose data is compromised.
The cumulative financial impact is substantial – $9.44 million per breach – allocating sufficient resources to defend against evolving cyber threats and protect national interests becomes a fraction of the financial fallout costs and an investment that reduces our spending in the long run. For Fiscal Year 2023, the government proposed a $10.89 billionxviii budget for cybersecurity, representing an increase of 10.67% from the previous fiscal year . These federal resources for cyber security are set to support a broad-based cyber security strategy for securing the government and enhancing the security of critical infrastructure and essential technologies.
Federal Readiness Against Cyber Threats
Federal agencies vary in their readiness to respond effectively to cyber incidents. While some have well-defined incident response plans in place, others may lack resources or established procedures, leaving vulnerabilities exposed. The lack of uniformity across agencies underscores the need for consistent and strong federal readiness.
In 2021, the US Government Accountability Office (GAO) found that only 26%xix of federal agencies had fully implemented all the critical elements of an incident response plan (IRP). Federal agencies can enhance their readiness and take proactive measures in defending against evolving cyber threats by incorporating the following:
- Prioritize Cybersecurity Investments: Allocate resources to invest in technology, personnel, and training exercises and drills to keep incident response teams prepared and identify areas for improvement.
- Develop a Resilient Incident Response Plan: Develop and maintain a resilient plan for detecting, responding to, and recovering from cyberattacks.
- Regularly Test and Update Plans: Ensure incident response plans remain effective and up-to-date by testing and revising them regularly.
- Share Cyber Threat Information: Facilitate the exchange of insights on cyber threats and incidents among federal agencies to enhance collective preparedness.
- Collaborate with the Private Sector: Forge partnerships with private-sector entities to advance cybersecurity technologies and share critical threat information.
- Standardize Incident Response: Adopt a consistent incident response framework across all federal agencies to ensure effective response.
- Enhanced Information Sharing: Strengthen the sharing of threat intelligence and best practices among agencies to bolster proactive defense.
- Streamline Reporting: Implement a centralized reporting mechanism for efficient incident reporting and data collection.
- Invest in Automation: Deploy automated incident response tools for faster threat detection, analysis, and mitigation, reducing response times and financial impacts.
- Forge Collaborative Partnerships: Partner with industry experts and private sector cybersecurity organizations to access advanced threat intelligence and expertise.
The financial impact of cyberattacks necessitates resilient incident response plans, collaboration, and amplified cybersecurity investments to protect our digital future. An incident response plan (IRP) serves as a fundamental pillar within any cybersecurity strategy that provides a roadmap for responding to and recovering from cyber-attacks.
A Call to Action for a Resilient Cybersecurity Future
A well-structured incident response plan can help organizations reduce the impact of cyber-attacks, minimize downtime, protect sensitive data, maintain customer trust, and ensure regulatory compliance. A comprehensive IRP includes several vital elements. Starting with the detection and analysis phase, it focuses on identifying and understanding cyber threats. Following this, the plan moves to containment, aiming to isolate and prevent the attack from spreading. The next step is eradication, which involves removing malware or other threats from systems. Then comes the recovery phase, where systems are restored to their initial state, and protective measures are implemented to prevent future attacks. Finally, the process concludes by documenting the incident and extracting insights for future improvements.
| Centralizing regulations and management: Ensure consistent best practices for incident response by centralizing regulations and management. Investing in automation: Expedite reactions to cyber-attacks by investing in automated incident response tools. Enhancing information sharing: Foster better threat awareness and response strategies through enhanced information sharing with the private sector. Increasing cybersecurity funding: Elevate the nation’s overall cybersecurity posture by increasing funding for research, development, and program implementation. |
Optimizing an IRP’s effectiveness involves essential best practices. Customizing the plan to fit the organization’s specific needs, considering factors like size, industry, and risk profile, is fundamental. Engaging key stakeholders, including IT, security, and business leaders, in its development and implementation is crucial. Regular testing keeps the IRP effective and adaptable to the ever-changing threat landscape.
A fortified incident response plan is the first step towards a robust defense against cyber threats and preventing financial ramifications, and federal agencies can take several strategic steps to bolster effectiveness: centralizing regulations and management, as proposed by CIRCIA; leveraging automation for swifter threat detection and response and reducing manual workload and potential delays.
Expanding Our Response Capacity with Technology
Technology has undoubtedly become an integral part of our lives, resulting in a world where we rely extensively on digital infrastructure. According to a report, every second, approximately 127 newxx devices connect to the internet. Digital connectivity has become an essential part of all individuals’ and businesses; it is not a choice anymore, but a necessity. Amidst this digital ecosystem, proactive measures and robust incident response plans are not only vital but non-negotiable against these insidious crimes. Incidents like SolarWinds and Colonial Pipeline are only two tiny reminders of the increasing prevalence and worsening financial consequences of cyberattacks.
To combat threats constantly evolving in sophistication within realistic resource constraints, federal agencies must identify ways to expand existing capacity. Automation can create more capacity for federal agencies to play their pivotal roles in securing critical infrastructure and sensitive data, improve information sharing, and scale the deep and predictive analysis necessary to safeguard the nation.
Increased dependency on digital infrastructure also increases the attack surface and the vulnerability of our nation – creating a desperate demand for robust cybersecurity measures. DX360°® Cyber Incident Reporter is a powerful and innovative tool for organizations to manage and respond to cybersecurity incidents – helping federal agencies to take a significant step forward towards enhancing incident response capabilities and keeping them a step ahead of cybercriminals. Built to CIRCIA compliance and adaptive to ongoing rulemaking or agency requirements, DX360°® Cyber Incident Reporter is the first and only app of its kind – enabling federal agencies to detect, respond, and recover swiftly and build a unified collaboration between industry and government.